
Hello everyone =]
A couple of weeks back I reported this phishing campaign attack to steemit.com.
I was on a little vacation in Florida at that time and on the subway heading back to my place in New York I was bored ,so I started reading around about previous security issues in Steemit.
I found this old article (and other similar ones) stating that plenty of accounts had been compromised due to users accidentally pasting their private keys in transfers memo and posts.
Some inexperienced users may not know this but those accounts and their funds are at risk, because even if you delete the private key accidentally published in the post/comment/transfer, the key is still stored forever in the blockchain, no matter of what edits you did afterwards to your post/comment (and you can't edit transfers)!
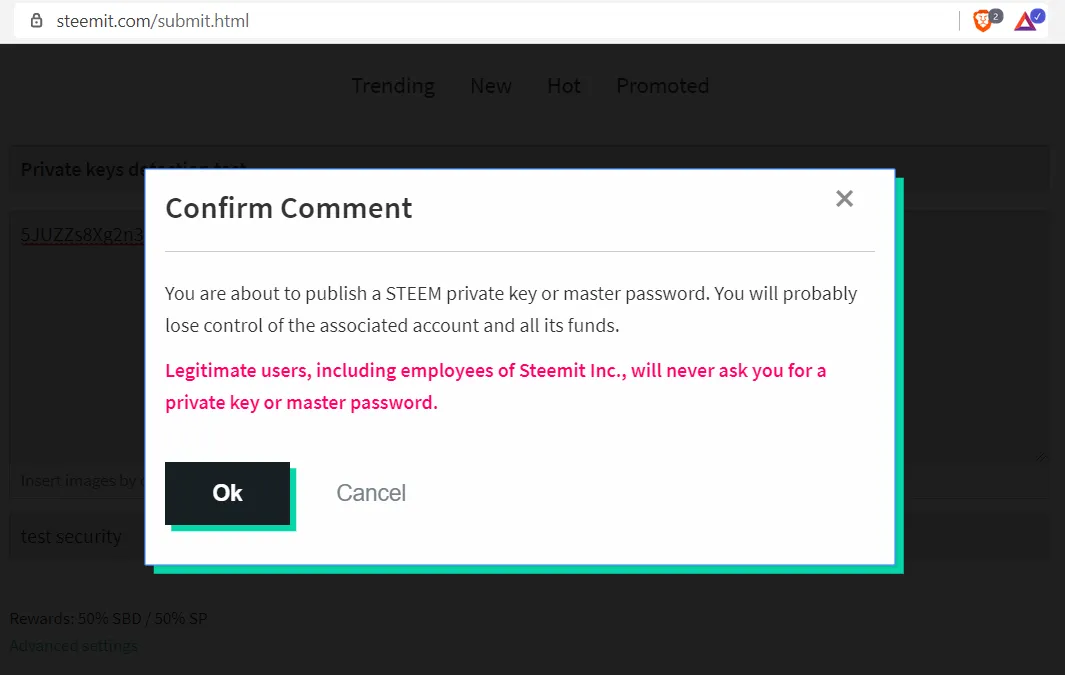
That led me thinking whether this is still an issue nowadays. So I tested steemit.com copying and pasting an (old) private key in a transfer memo, in a comment and in a post.
As result, a popup came up telling me that if I proceeded I was going to compromise my account. That's good!
 By the way, use Brave browser for better performance and security!!
By the way, use Brave browser for better performance and security!!The problem though is that other STEEM blockchain User Interfaces and Apps (eg. Partiko, Esteem, etc) do not have this leak prevention mechanism in place yet!! (I tried this myself)
So I then decided to write a script that scans the entire steem blockchain on a couple of threads in order to verify whether there are still users that after accidentally leaking their private key did not reset them.
I ran the script for a couple of days and here follows the first partial result (after scanning only 11 million blocks).
I found:

- - 2x PRIVATE ACTIVE KEYS.
- - 3x PRIVATE MEMO KEYS.
- - 39x PRIVATE POSTING KEYS.
The active keys leak is more serious as an attacker can delegate or transfer funds away from the owner's wallet.
One of the accounts accessible with those active keys has 692.702 STEEM and 3054 followers! And some accounts using a compromised posting key have thousands of followers as well.
These would be interesting preys for an attacker!


.1. So far I only scanned about one forth of the entire STEEM blockchain. Next week I'll resume the scanning (I'm currently on holiday) and keep you posted with the results.
.2. I have also been working on a version 2 of the STEEM blockchain scanner. { By the way, any suggestions for the bot name?? =] }

My new bot will run 24 hours a day, 7 days a week, to automatically detect when users accidentally leak their keys.
The bot will automatically do the following when a private key is detected:
- Detect the type of key trying to authenticate into Steemit.
- For posting keys it will comment on the user's last post warning them that they compromised their posting key
- For active keys it will put all liquid steem/sbd into savings and warn the user
- For owner keys it will reset their account and the new keys will be privately sent to @guiltyparties so that he can give them back to the owner when he/she proves that the account is his/her.
- Every week my bot will publish a post with some stats and updates on the compromised accounts found scanning the blockchain.
Please feel free show your support on those posts in order to keep the bot with enough RC to perform its operations (comments, transfers to savings, etc).
Note that my bot (already in its 1st version) checks all operations published into the STEEM blockchain, not only comments and posts as other bots did in the past. This is because we don't know what Frontends and DAPPS will be created and how they will use the blockchain in the future. Meaning that private keys could still be accidentally placed in other fields of the data published (forever) into the STEEM blockchain. My bots will detect those new fields too (analyzing the raw JSON data) and prevent compromised keys from ending in the wrong hands.

If you'll want to test it out yourself as well, you will be able to do so with a dummy account or using a non-owner key so that you can then easily reset them all afterwards.
On a similar note..
I am currently re-writing those bots in order to make them faster / more reliable / more scalable and implement some other improvements that are on my backlog. I also have other ideas for other brand-new bots. So.. stay tuned!

And since it's tax time already, feel free to re-use my free tool to calculate the sum of your incoming transactions and rewards. Enjoy! =]
See you soon,
Gabe
